What Is Shadow IT Policy and Its Worth to Your Organization?
In most organizations, there's an extensive "shadow IT" network, also known as a shadow IT system.
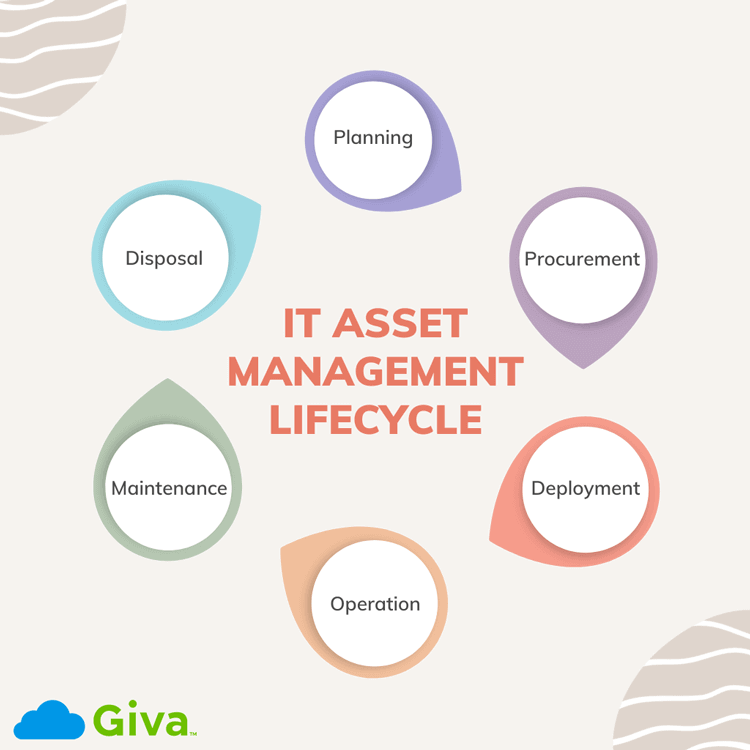
In every mid-size and large organization, there's usually an extensive interconnected network of approved software solutions and systems. In some cases, these software or hardware solutions are proprietary and have been developed exclusively for that organization.
However, since the turn of the century, there has been rapid proliferation of cloud-based software, hardware, apps, and other systems that organizations are now using. Businesses are often spending anywhere from tens to hundreds of thousands of dollars annually on software, hardware, and IT vendors and IT Service Management (ITSM) partners.